Hiram College PO Box 67 Hiram, Ohio 44234 330-569-3211
Hiram College
Intimate learning. Global reach.
Instructor Roger F. Cram
![]() in Modern Business Cultures
in Modern Business Cultures
Hiram College PO Box 67 Hiram, Ohio 44234
330-569-3211
On-Line Courses - Use Assigned
Learninghouse-Moodle Syllabus
and the four below PowerPoint
Presentations:
Atoms, Energy, and
Electricity Part I
Atoms, Energy, and Electricity
Part II
Atoms, Energy,
and Electricity Part III
Atoms, Energy,
and Electricity Part IV
Classroom Course for Hiram College, Tri-C, and LCCC: Use the below syllabus and the four PowerPoints above.
|
INDT 327-51
|
Fall
2014- WEC
6:00 pm to 10:00pm
Course Syllabus
Click
here to go to Disney World
Click here for extra credit
Click here for a prize
Session
1
This first week
you will be introduced to different types of crime occurring in corporations.
You will learn about what happens in our society when major technological
advancements occur - who is benefited and who is harmed. You will be introduced
to your first list of Electronic Crime vocabulary words and you will begin your
study into the characteristics of electricity that allows criminals to steal
money and data.
Select Class Teams:
Readings:
| First Assignment - Read before coiming to class: Technologies, Social Media, and Society – Read Article 1 in 13/14 edition; Article 1.1 in Unit 1 from the Twentieth Edition: Five Things We Need to Know About Technology There will be a class discussion on this important article. You are not being assigned a paper to write. | |||||
Managing the Risk of Fraud and Misconduct – Read
| |||||
| Electricity Demystified - Read Chapter 2 – Charge, Current, Voltage, and Resistance |
| How Big is An Atom? 1:16 | |
| What is Electricty? | |
| Source: Nova Science NOW |
"Atoms, Energy, and Electricity Part 1" (Click) This PowerPoint is designed to supplement your assignment in Electricity DeMystified. Upon arriving at the website, click on Atoms, Energy, and Electricity Part I. A PowerPoint presentation should download to your computer. If you are asked for a password, ignore the request
Quizzes:
Week One - Vocabulary. Look up the definitions to the listed
vocabulary words and print them on a sheet of paper. You may use the on-line
dictionaries provided below or your own source. Bring these definitions to
Session 2, printed, and hand them in.
Hacker's Dictionary
FOLDOC Dictionary
Enter your term on the
top and click search.
The Jargon File
Click on "Glossary" in Section II on the left hand side.
The vocabulary words on the quiz are listed below. Bring your definitions to Session 2 and hand them in.
Virus
Worm
Hacker
Trojan Horse
Cracker
Social Engineering
Phreaker
Firewall
Backdoor
Dumpster Diver
Presentations: None
For Next Week:
Hand in the Vocabulary Quiz from Session 1, printed. Hand in the
following essay:
Essays: Technologies, Social Media and
Society
Five Things We Need to Know About Technology Change
The word processing, spell checking, grammar correcting PC was a blessing to writers and students everywhere. However, typewriter companies went out of business and our children are not learning how to spell. The hand-held calculator was a God send over the slide rule. The calculator was small and easy to carry, helped people calculate the best bargains at a grocery store, helped engineers to do complex calculations on job sites, and made math calculations a breeze for students increasing their accuracy. However, our children's mathematics skills are shrinking.
In the olden days oil was used in lamps to provide light for our homes. When the electric light bulb was invented, it should have put the oil companies out of business, but the invention of the oil furnace kept them alive. When the natural gas furnace was invented the oil companies should again have seen their demise, but the invention of the automobile and airplane saved them again as gasoline provided a new demand. What will happen to the oil companies when solar and electric cars are perfected?
You are going to school on line using your PC for this course. A few years ago the only school available was a classroom or a correspondence course where individual lessons were delivered to you through the mail. Correspondence course companies are now out of business. Some colleges are closing their doors or offerring on line courses and remote learning sites to compete with the changing demand for education.
Using any two of the Five Things We Need to Know About Technology Change, describe a product or service in your life, family, or job that illustrates a clear example of your two choices.
Answer this in not less than 500 words.
Session 2
This second week will take you into some of the problems and future
concerns with your social networks, like Facebook. Are we being manipulated and
controlled? Is all of our personal information on Facebook, now the largest
human behavioral data base in the world, going to cause us problems in the
future? Will our private and highly personal information be sold or compromised?
Our smartphones, are they actually making decisions for us like which movie we
want to watch, which restaurant do we want to go to, and which products or
services are we going to use? Are all our Internet clicks recorded? Is our
location always available to someone through GPS recorded tracking?
Corporate fraud will be explored again, but this time through financial reporting fraud. Can money be stolen from a corporation by minipulating expense and revenue figures? Since 80% of corporate fraud occurrs from employees, are top management as involved as other lower-stature employees?
As we advance our way toward understanding how
magnetic signals carrying personal information are intercepted and stolen by
hackers, we will explore voltage, amperes, and resistance through Ohm's Law.
This involves only simple arithmetic like 6=12 / 2 or 12 = 6x2. For those of you
afraid of math, we go no further than Ohm's law, despite what your text book
Electricity DeMystified may present.
Due this Session:
(1) Vocabulary words assigned during our last session
(2)
Essay assigned Session 1
Technologies, Social Media and
Society - Five Things We Need to Know About Technology Change
Readings:
Technologies, Social Media, and Society
| |||||
Managing the Risk of Fraud and Misconduct – Read
| |||||
| Electricity Demystified - Read Chapter 3 – Ohm's Law, Power, and Energy |
In connection with Chapter 6 in Electricity DeMystified, view the following short videos designed to help you understand this material.
AC Current Through Magnetism
Electromagnetic Spectrum Source: Rocketboom.com
Electromatic Waves and the Sun Source: PBS Video
The Earths Magnetic Lines of Flux Source: Youtube.com
Atoms, Energy and Electricity Part II (Click) This PowerPoint is designed to supplement your assignment in Electricity DeMystified. Upon arriving at the website, click on Atoms, Energy, and Electricity Part IV. A PowerPoint presentation should download to your computer. If you are asked for a password, ignore the request.
After or before reading Chapter 3 in Electricity DeMystified, view the following short videos designed to help you understand this material.
|
View
Atoms, Energy and Electricity
Part II (Click) This PowerPoint is designed to
supplement your assignment in Electricity DeMystified. Upon
arriving at the website, click on Atoms, Energy, and Electricity
Part II. A PowerPoint presentation should download to your
computer. If you are asked for a password, ignore the request.
Class
Discussion: In Technologies, Social
Media, and Society there is an article entitled What
Facebook Knows. On page 24 in the 13/14 edition, and on
page 49 of the Twentieth Edition, find the section titled
"Social Engineering" and described how Facebook was used to
secretly increase organ donors and influence elections by
getting more people to vote.
Discuss how do you feel about the possibility of Facebook or other social media being used to secretly influence your choices? Do you feel you are being unknowingly manipulated if this technique was used to sell products or influence your social or political decisions? Has this happened to you?
Quizzes:
Week Two - Vocabulary. Look up the definitions to the
listed vocabulary words and print them on a sheet of paper. You
may use the on-line dictionaries listed below or your own
source.
Hacker's
Dictionary
FOLDOC Dictionary
Enter your term on the top and click search.
The
Jargon File
Click on "Glossary" in Section II on the left
hand side.
The vocabulary words on this quiz are:
ISP
Shoulder Surfing
Twitter - What is this
organization; what does it do?
Facebook - What is this
organization; what does it do?
Bit
Byte
Barf or
Barfulation
Code Police
CEO - See Chapter 2 in
Managing the Risk of Fraud and Misconduct
U.S. GAAP -
See Chapter 2 in Managing the Risk of Fraud and Misconduct
Presentations:
Essays:
There are two essays assigned this
week. (1)
Who is Kevin Mitnik This assignment is to be
turned in Session 3. (2) Research Paper/ Essay: How Modern
Technology Has Negatively Impacted Your Life. This
paper is to be double spaced and no less that 750 words.
This assignment is to be turned in Session 4.
How Modern
Technology Has Negatively Impacted Your Life
Almost all of you have been exposed to the problems
associated with electronics in the workplace. This
course deals with how electronics (computers, software,
pagers, cell phones, laptops, e-mail, Bloggs) improperly
implemented into the workplace causes stress, turnover,
poor moral, loss of efficiency and effectiveness,
undermined corporate structure, and encourages internal
crime. Your research paper should involve your personal
experiences with this problem. By understanding how and
why these things occur, you will hopefully become better
managers.
If you are a housewife or househusband and have never experienced the negative aspects of electronics in the workplace, perhaps your social contacts have unfavorably changed for the same reason. Many persons have lost friends because of excessive participation with American on Line (AOL). Chatting on AOL, being addicted to their garage sales, addicted to computer games with partners in remote locations, or just surfing the Internet have so involved some families that their friends and other former social contacts have all but been replaced with these new electronic acquaintances. Have you ever been the victim of identity theft? Children spending hours on the Web have altered family social activities. Perhaps your children have had unpleasant experiences associated with the total proliferation of adult material. Possibly you have become the victim of computer fraud over the Internet.
If you are a traditional student and have not yet been employed in any of today’s busy electronic industries, perhaps electronics in your high school classes or in your social circles have had a negative impact on your morale, self-esteem, or social circles. Have you ever been the victim of bully texting? Perhaps an electronic dating service has exposed you to a less than desirable experience. Possibly the need to use computers in college and keep up with all the modern changes in software are causing you problems. If none of the above events have occurred in your life, you may do research into the negative aspects of computers in society and write a paper on your findings.
The research paper is to be no less than 750 words (about 3 pages double spaced). Actually, it is not a research paper, but rather a report of your personal experiences as they relate to the core-concepts of this course.
Write a 500 word essay on the subject: Who
Was Kevin Mitnik? Turn this Essay in at the next
class session.
Please double space this essay. You may use
your own sourses of reference or refer to the
links below.
Session 3
When automation at the workplace
started in the 1950s and 1960s, many people projected that the use of computers
would allow a person to do one days work in only three or four hours. This would
greatly increase the worker's leisure time. As it turns out, when computers did
allow one worker to finish his/her tasks in a few hours, instead of going home,
the worker was told to stay at work doing the tasks of two or three workers.
This not only increased each worker's responsibility, but reduced jobs.
Employers now had a better means to spy on employees through technology. This
topic will gradually be covered throughout the rest of this course.
What is Phishing? How can we detect it? What is Cybersquatting? What is
Social Engineering? Are we ever personally exposed to these activities? Can
these activities be spotted by us, the users, before and damage is done to our
computers or bank accounts?
The
above topics will be studied this week along with getting closer to
understanding how criminals intercept our computer and cell phone signals to
complete their evil deeds. Read the Hacker Newspapers listed below for some
fascinating events occurring with Verizon last month. Are your cell phone
conversations being recorded? Are your cell phone numbers being compared to
those phone number called on terrerist's cell phone records?
Pizza Party - supplied
by the professor.
Due this Session:
(1) Vocabulary words assigned during our last session
(2) Essay assigned last session on Kevin Mitnik
Readings:
| Technologies, Social Media, and Society - No assignment this week. | |||||
Read the following articles from the Internet:
| |||||
Managing the Risk of Fraud and Misconduct – Read
| |||||
| Electricity Demystified - Read Chapter 4 – Simple DC Circuits Pages 61 to 72 |
Mysterious Magnetic Fields 1:38
Basic DC Series Circuit 4:23
Simple Series and Parellel Circuits 8:35
AC & DC
Resistance
What is electricity
Ohm's Law
View
Atoms, Energy and Electricity Part III Click) This PowerPoint is
designed to supplement your assignment in Electricity DeMystified. Upon
arriving at the website, click on Atoms, Energy, and Electricity Part III. A
PowerPoint presentation should download to your computer. If you are asked
for a password, ignore the request.
Quizzes:
First take-home
quiz issued in class. To be turned in Session Four.
Week 3, Vocabulary.
Look up the definitions to the listed vocabulary words and type them into
the answer spaces provided. You may use the on-line dictionaries listed
below or your own source.
Hacker's
Dictionary
FOLDOC
Dictionary - Enter your term on the top and click search.
The Jargon File - Click on "Glossary" in Section II on the left hand
side.
The vocabulary words on this quiz are:
Botnets
Wall (as used on Facebook) Uploading
Downloading
Uploading
Browser
Phishing
Spy ware or malicious software
Cybersquatting or Typosquaters
Blog
Discussion:
Electromagnetic Waves
If you understood the presentation Atoms, Energy, and Electricity Part III then you have a remarkable knowledge about an incredible phenomenon that we use hundreds of times a day, but had no idea about its complexity.
Thousands of electromagnetic waves are passing through our bodies from all the radio and television signals, everyone's cell phone conversations, everyone who is texting, all Wi-Fi locations, all police cars, fire trucks, and ambulances, all aircraft, the military, gamma rays, ultraviolet, infrared, and thousands of others. It's very good we can't see these electromagnetic waves because there are so many of them we wouldn't see much of anything else.
With much of our personal and proprietary information available through the interception of electromagnetic waves, are you a little nervous about your credit cards, bank accounts, securities, and other personal information? Can your medical records be easily hacked? Can money from your checking accounts be transferred in the middle of the night while you sleep?
While your bank manager is at her desk entering bank account and credit card numbers of customers into her computer, someone in a van stopped in the bank's parking lot is busy intercepting these signals and stealing all this data. You see, every time the bank manager strikes a key on her computer keyboard, it sends an electric signal to the computer and the computer screen. Did I say an electrical signal was sent? Yes, and it created a electromagnetic wave as all electrical signals do, and this electromagnetic wave left the bank manager's key board and traveled through space at the speed of light. Yes, the van in the parking lot has an antenna (wire, conductor) that picks up these electromagnetic waves from the bank manager's keyboard turning them into alternating currents that can be tuned to duplicate each key stroke, each password, each bank account code, and each credit card number.
There are companies that do not have enough computer space to manage their operations. Instead of spending thousands of dollars on more computer memory and operating software, they intercept the computer Wi-Fi signals from other companies and actually utilize their unused computer memory, storage space, and even software. The best kind of antenna for intercepting computer system Wi-Fi signals is made from an empty Pringles potato chip can. The Pringles can has aluminum foil on the inside that creates alternating electric currents when passed over by a company's Wi-Fi electromagnetic waves traveling from their router through space at the speed of light. Feel safe?
Discuss in class how understanding the
electromagnetic wave phenomenon presented in my PowerPoint presentation
Atoms, Energy, and Electricity Part III made you feel? Is this a
revelation to you? Did you already know this? Are you feeling nervous for
your security? Are you worried about Identity theft? Please answer
this Forum in no less than 500 words and be sure to comment on two postings
from your fellow classmates.
Presentations:
Essays:
For Next Week:
This week we
will finally understand how cyber criminals intercept proprietary
information like passwords, credit card numbers, and transferring money from
bank accounts. It is interesting to note that one rarely reads in the
newspapers or views on TV news programs stories about money being stolen
from banks through hackers and cyber criminals, yet this type of electronic
crime is very common. If you were the CEO of First National Bank and your
customers were having money stolen from their accounts by hackers, would you
want that published in a newspaper or on the TV news? Probably not, for many
of your customers would close their accounts. If the police located a cyber
criminal hacking into your customer's accounts, would you want that person
arrested and prosecuted so all the details about the trial would be in the
newspapers or on the evening news? Again, your bank would lose many
customers.
People today are so use
to texting, using email, participating in chat rooms and other forms of data
communications that it is often difficult to tell if your friends or
associates are real people. Are these continuous cyber relationships harming
our social person-to-person interaction skills? Is the person we are
communicating with who they say they are or, possibly, even real?
In order to protect our companies and employers we need to be familiar with
building or maintaining an
integrated and comprehensive
compliance program capable of assessing risks, preventing and detecting
misconduct, and evaluating its effectiveness. After all, being aware of
electronic crime, preventing and detecting it, and improving policies and
procedures to prevent its recurrence is probably why your are taking this
course.
All of the subjects mentioned above and
more will be covered this week as we continue to pursue our journey into
understanding the world of electronic crime.
We will be using the following two publications in class for sessions 4, 5, and 6
http://www.theprosandthecons.com/articles/GDZ%20WCCF%20Ethics.pdf
http://egov.oregon.gov/DAS/SCD/docs/antifraud.pdf
Technologies, Social Media, and Society
| |||||
Managing the Risk of Fraud and Misconduct - Read Part III
| |||||
| Electricity DeMystified - Read Chapter 6 – What is Alternating Current? pages 119-130 |
In connection with Chapter 6 in Electricity DeMystified, view the following short videos designed to help you understand this material.
AC Current Through Magnetism
Electromagnetic Spectrum Source: Rocketboom.com
Electromatic Waves and the Sun Source: PBS Video
The Earths Magnetic Lines of Flux Source: Youtube.com
Some Video Fun:
Electronic Gadgets
Fun with Magnetism
An Electric Motor
A
simpler motor
A Blond
Girl Motor
How to Hack a POP
Machine
Reprogram POP
Machines
Elevator Hack
Inside
a 9V Battery
Combination Lock Pick
Locked out of your
car?
Car
Lock Myth Busted
Hacker's Dictionary
FOLDOC Dictionary - Enter your term on the top and click search.
The Jargon File - Click on "Glossary" in Section II on the left hand
side.
The vocabulary words on this quiz are:
Risk-Specific Compliance Managers - See Chapter 6 - Managing the Risk
of Fraud and Misconduct
Frequency - Chapter 6 - Electricity
DeMystified
Wavelength - Chapter 6 - Electricity DeMystified
Virtual Reality or Virtual Society - Article: Relationships, Community,
and Itenity In the New Virtual Society in the text Technologies,
Social Media, and Society
Micro-Coordination - Article:
Relationships, Community, and Itenity In the New Virtual Society in the
text - Technologies, Social Media, and Society
Gabriel
Gnarly
Clone
Fried
Iron Box
Class Discussion: The Movie Hackers
Towards the end of the movie Hackers, a war was
waged on the main frame computer designed to sink the oil tankers by
hundreds of computers from all over the world attacking simultaneously. What
is the hacker term for this type of an attack? You have been told in
this course that 80% of corporate electronic crime comes from insiders. How
does this fact pertain to the filmHackers? Do you see any similarity
between the movie Hackers and the Kevin Mitnik story?
Presentations:
Essays: A Study in Communications Abuse - The
Personalities and Motivations of Telephone Phreakers
Go to the links below and learn about Captain Crunch. Learn about the relationships of Captain Crunch (Draper) with Kevin Mitnick, Steve Jobs and Steven Wozniak from Apple Computer (small world).
After viewing the above videos, write in not less than 500 words, what do you think of the hacker's or phreaker's culture, personality, beliefs, and egos? Is this a game? A challenge? Listen to what these famous hackers - Mitnick, Draper, Wozniak - say to justify their crimes. Write a personality profile of Phreaker's as you are able to obtain from the above videos.
Turn this essay in at the next class session.
For Next Week:
Session
5
Due this Session:
Vocabulary words assigned during our last session,
Essay on the
Hacker's Personality
Readings:
We will be using the following two publications
in class for sessions 4, 5, and 6
http://www.theprosandthecons.com/articles/GDZ%20WCCF%20Ethics.pdf
http://egov.oregon.gov/DAS/SCD/docs/antifraud.pdf
| The
Hacker's Home Page (This site is provided to study the
hacker community and philosophy and to make you aware of
what tools are available.) | |||||
Technologies, Social Media, and Society:
| |||||
Managing the Risk of Fraud and Misconduct
| |||||
Electricity Demystified
|
In connection with Chapter 4 in Electricity DeMystified, view the following short videos designed to help you understand this material.
Hacking Culture Videos
Fraud in vending machine hacking
Hacking a pop machine 0:54
What is a Hacker? 3:33 (listen to this hacker's
culture and philosophy)
Videos:
Hackers.
This movie is 107 minutes long, rated PG-13, made in 1995, and stars
Jonny Lee Miller,
Angelina Jolie,
Jesse Bradford. Hackers
can be currently rented from Amazon.com for $2.99.
Click here to view this rental site. YOUR WRITING ASSIGNMENT FOR
THIS WEEK WILL BE ON THE VIDEO HACKERS.
PowerPoint
Presentations:
Atoms, Energy and Electricity Part IV (Click) This PowerPoint is designed to supplement your assignment in Electricity DeMystified. Upon arriving at the website, click on Atoms, Energy, and Electricity Part IV. A PowerPoint presentation should download to your computer. If you are asked for a password, ignore the request.
Quizzes:
Second take-home quiz issued in class.
It is popsted on the Website. To be turned in Session 6.
Week 5, Vocabulary. Look up the
definitions to the listed vocabulary words and print them on a sheet
of paper. You may use the on-line dictionaries listed below or your
own source. Some of the terms below can be found in hacker
dictionaries and in the videos about Captain Crunch.
Many of the below terms were taken from articles in Technologies, Social Media, and Society. Please do not simply tell me what a definition stands for (like PDF), tell me what it is and what it means.
Blue Box
Malware
Encryption
Slammer Worm
U.S. Power
Grid
PDF Files
Denial of Service Attack
ESN / MSN
War
Dialer
USB
Class Discussions:
Modern Technology vs. Toys
John T Draper, known as Captain Crunch, was the nickname of a hacker in the 1970s who shut down the eastern half of AT&T's telephone long distance switching system. He accomplished this task by blowing a whistle found in a Captain Crunch cereal box into a telephone.
The frequency of the whistle was about 2600 cycles per second, or as we now know, 2600 Hz. 2600 Hz is well within the range of human hearing being between 20 Hz up to 20,000 Hz.
Do you remember that one of the hacking organizations in New York listed each week on our schedule is called 2600? I wonder why they use that name?
AT&T decided to save money by allowing their voice and data signalling frequencies to be in the same frequency range. A 2600 Hz tone is a little higher in pitch than a dial tone and was used by AT&T's long distance switching stations to look for an open long distance line. Empty or unused long distance lines would look for a newly dialed long distance call that needed to be connected to the long distance network. AT&T's equipment generated a 2600 Hz tone when a long distance call was placed and the AT&T switching station looked for lines generating this tone. Once located, the switching station connected the call generating the tone to the long distance network and completed the call.
It turns out that the Captain Crunch whistle found in the cereal box generated an almost perfect 2600 Hz tone. Guess what happened?
Go to the links below and learn about Captain Crunch. Learn about the relationships of Captain Crunch (Draper) with Kevin Mitnick, Steve Jobs and Steven Wozniak from Apple Computer (small world).
Discuss what do you think of a cereal whistle being used to shut
down AT&T? In a previous week, I mentioned that an empty
Prinkle's Potato chip can was an excellent antenna for intercepting
corporate Wi-Fi signals and utilizing their computers.
Cereal box whistles,
potato chip cans - what's going on here?
Presentations:
Essays:
For Next Week: Vocabulary list from
Session 5. Quiz # 2.
Session 6
Hors d' oeuvres
Party - supplied by
the students.
Due this Session:
(1) Vocabulary words
assigned during our last session
We will be using the following two publications in class for sessions 4, 5, and 6
http://www.theprosandthecons.com/articles/GDZ%20WCCF%20Ethics.pdf
http://egov.oregon.gov/DAS/SCD/docs/antifraud.pdf
Textbook Assignments:
| Technologies, Social Media, and Society - No assignments | |||||
Internet Articles:
| |||||
Managing the Risk of Fraud and Misconduct – Read
| |||||
| Electricity Demystified - Read Chapter 10 – What is Magnetism Pages 231 to 236, and pages 244 to 247 |
Articles:
Please read the
following article. You are required to write a short essay on a
portion of this article.
Managing Antifraud Programs and Controls by the American Institute of Certified Public Accountants, Inc. New York, NT.
Top 5 Hackers Publications, Web Sites, Etc.
The Solar Winds and Our Magnetic Field 4:44 The Earth's Magnetic Field is Collapsing 3:39 The Solar Winds Effect on Earth 4:44 The Rise of Drones - Netflix
Quizzes:
Take-Home Final Exam issued. It is on the Website. To be turned in Session 7.
Week 6, Vocabulary. Look up the
definitions to the listed vocabulary words and print them on a sheet
of paper. You may use the on-line dictionaries listed below or your
own source.
Hacker's Dictionary
FOLDOC Dictionary -
Enter your term on the top and click search.
The Jargon File - Click on "Glossary" in Section II on the left
hand side.
Some of the terms below can be found in hacker dictionaries.
Many of the below terms were taken from articles Technologies, Social Media, and Society and other reading assignments. Some of the words and definitions are found in future assignments regarding government spying. Please do not simply tell me what a definition stands for (like PDF), tell me what it is and what it means.
The vocabulary words on this quiz are:
Tracking files
Third-party tracking files
Beacons
Flash
cookies
BlueKai (the company)
Flux
Ampere's Law
Solar
Winds
Cyberbullying
Code of Conduct
Class Discussions: Solar Winds
Many hackers have proclaimed, some testifying before Congress, that the easiest way to shut down the Internet is to hack into and disable the nations power grid. No electricity to homes and business, no Internet.
The two videos below were part of your material this week to reinforce your reading material in Electricity DeMystified. They are listed here again for your convenience.
| The Solar Winds and Our Magnetic Field | |
| The Earth's Magnetic Field |
The earth's magnetic fields when struck by the solar winds from the sun can shut down the power grids in many countries. It sounds like the sun can perform some very sophisticated hacking! What do you think of all this? Protecting ourselves from hackers and cyber-criminals is difficult enough, but how do we protect ourselves from the solar winds?
Are you beginning to see how mysterious and powerful magnetic fields can be?
Presentations:
Essays:
Creating a
Positive Workplace
Management Antifraud Programs and Controls
Managing Antifraud Programs and Controls
by the American Institute of Certified Public Accountants,
Inc. New York, NT.
The above article is extremely valuable to this course and is very well written. It comes from the American Institute of Certified Public Accounts. Keep this article handy and read it carefully. It can be effectively used for a portion of your final exam.
For this reading assignment and essay, write in not less than 750 words on pages 5 through 10 of Management Antifraud Programs and Controls, a summary of creating a positive workplace environment through hiring practices, discipline, attitude, and training. Then, if you are able, continue writing about your experiences in a job where such positive attributes were not in place.
Submit this essay at the next class session.
For Next
Week:
Turn in
Essay - Creating a Positive Workplace. Turn in vocabulary words.
Turn in Quiz #2. Turn in Final Exam.
Session
7
Due this Session:
Vocabulary words assigned during our last session,
final exam, Quiz #2
Readings:
| Technologies, Social Media, and Society read Know Your
Rights – Article 22 in the 13/14 Edition and Article 8.2 in the
Twentieth Edition. Technologies, Social Media, and Society - Read How to Spot the Future - Article 30 in Edition 13/14, Article 9.1 in the Twentieth Edition. | |||||
Managing the Risk of Fraud and Misconduct
| |||||
| Read Internet Article: Why Does the US Government Care More About Spying On Your Email Than Getting You A Job? |
Week 7, Vocabulary. Look up the definitions to the listed vocabulary words and print them on a sheet of paper. You may use the on-line dictionaries listed below or your own source.
Hacker's Dictionary
FOLDOC
Dictionary - Enter your term on the top and
click search.
The Jargon File -
Click on "Glossary" in Section II on the left hand side.
Some of the terms below can be found in hacker dictionaries.
Many of the below terms were taken from Technologies, Social Media, and Society and other reading assignments. Some are definitions and terms you need to know to understand upcoming articles. Please do not simply tell me what a definition stands for (like PDF), tell me what it is and what it means.
The vocabulary words on this quiz are:
Fourth Amendment
File sharing
Domain name
URL
First
Amendment
ISP Memorandum
Time-shifting-
Whistle
blower - Chapter 10
Exit Interviews - Chapter 10
Web-based
reporting system
Class Discussion:
OTHER COURSE INFORMATION
Text Books
Technologies, Social Media, and Society - 13/14 Edition or the Twentieth Edition
Electricity Demystified,
2nd Edition McGraw Hill
Managing The Risk of Fraud and Misconduct
McGraw Hill
Assignments and Quizzes
30% - Quizzes: 15% - Quiz One issued Session 3. 15% - Quiz Two
issued Session 6
20% - Essays: 5% - How Modern Technology Has Negatively Affected Your Life
5% - Who Was Kevin Mitnik?
5% - Creating A Positive Workplace
5% - A Study in Communications Abuse - The Personalities and Motivations of
Telephone Phreakers
10% - Research Paper: Future Hacking Trend Based On Media Release
10% - Class participation and attendance
12% - 6 Vocabulary tests = 2% each
18% - Final Exam:
Grading Policy
Research Paper - 10%
Two quizzes - 15% each =
30% Quiz One issued Session 3. Quiz Two issued Session 5.
Essays - 20%
Vocabulary Tests = 2% each total 12%
Final Exam - 18%
Attendance and Class Participation
- 10%
After Completing This Course Students Will Be Able To:
|
Students will write a research paper detailing how modern-3day electronic has negatively impacted their lives. (Stolen identity, credit card fraud, slander on Facebook, email flaming, etc.) | |
|
Students will analyze from the criminal’s perspective by examining what types of reasoning justifies electronic crime in the mind of the perpetrator and what motivates employee’s to commit corporate crime? | |
|
Students will research changes in corporate cultures that provide opportunities for internal crime and the employee stress that encourages such activity. | |
|
Students will be required to consider all the material presented in the course and develop an “addhock” organization or company with highly effective electronic crime deterrents interwoven with personnel policies and procedures encouraging efficiency, trust, and considering the human factor. | |
|
Student will experiment with various forms of induction and magnetic fields thus creating an understanding of how many electronic secrets are intercepted and stolen. | |
|
Students will explain the electronics involved as hackers, phreakers, and telephone criminals go about their trade stealing information in this digital age. | |
|
Students will
investigate and describe various forms of electronic crime by studying how
such events occurred in corporations, various governments, different
branches of our military, several | |
|
Students will
explore what motivates people to commit corporate crime, what kinds of beh
avior and personalities indicate potential criminals, which personality
characteristics are indicative of anti- |
Vocabulary Quizzes
Throughout this course we will be studying vocabulary
related to electronic crime. Each week you will be given ten vocabulary words
relevant to your studies assigned. Below, for your convenience, are three
websites serving as dictionaries for such terms. Each week please turn in to
your instructor your ten vocabulary words from the previous week's assignment.
Give complete definitions, not just what a term like "URL" srtands for. Make
sure you understand your submitted definition. If it is extremely complicated
and obviously copied from another source, I may ask you to explain your
submisson.
Hacker's Dictionary
FOLDOC Dictionary
Hacker's
Dictionary Two
The Jargon File
Click on "Glossary" on the left hand
side.
Field Trip
The research paper/essay is to be at least 750 words, printed, and double-spaced. Actually, it is not a research paper, but rather a report of your personal experiences as they relate to the core-concepts of this course.
Almost all of you have been exposed to the problems associated with electronics in the workplace. This course deals with how electronics (computers, software, pagers, cell phones, laptops, e-mail, Bloggs) improperly implemented into the workplace causes stress, turnover, poor moral, loss of efficiency and effectiveness, undermined corporate structure, and encourages internal crime. Your research paper should involve your personal experiences with this problem. By understanding how and why these things occur, you will hopefully become better managers.
If you are a housewife or househusband and have never experienced the negative aspects of electronics in the workplace, perhaps your social contacts have unfavorably changed for the same reason. Many persons have lost friends because of excessive participation with American on Line (AOL). Chatting on AOL, being addicted to their garage sales, addicted to computer games with partners in remote locations, or just surfing the Internet have so involved some families that their friends and other former social contacts have all but been replaced with these new electronic acquaintances. Children spending hours on the Web have altered family social activities. Perhaps your children have had unpleasant experiences associated with the total proliferation of adult material. Possibly you have become the victim of computer fraud over the Internet.
If you are a traditional student and have not yet been employed in any of today’s busy electronic industries, perhaps electronics in your high school classes or in your social circles have had a negative impact on your morale, self-esteem, or social circles. Perhaps an electronic dating service has exposed you to a less than desirable experience. Possibly the need to use computers in college and keep up with all the modern changes in software are causing you problems. If none of the above events have occurred in your life, you may do research into the negative aspects of computers in society and write a paper on your findings.
Final Exam Fall 2014
The final exam is a take-home final, mostly essay, and will be issued during class session 6. You will have two weeks to complete your take-home, open-book final. It will be an essay final involving the concepts presented in all the articles, lectures, films, and other media presented in class. Below is last year's final exam as a possible sample:
You are a new CEO in a 25-year old company with 100 employees. Your company makes computer boards for PCs. It is your job to create an empowered work force with the security needed to protect the piracy and theft of corporate secrets and assets. Because you are a new CEO and are starting new procedures and policies, you are creating change. This change will create insecurities among some employees, reveal some Hems and Haws, some Sniffs and Scurries. According to our bible, in the article MANAGEMENT ANTIFRAUD PROGRAMS AND CONTROLS, several measures are needed for security and company efficiency during times of change, both to protect the company and to foster empowerment.
Write a 5-page
(minimum 1200 words) paper using information from Who Moved my Cheese,
MANAGEMENT ANTIFRAUD
PROGRAMS AND CONTROLS, White-Collar Crime, and any pertinent 3 articles assigned in class from
Computers in Society, and present your plan as the new CEO to create an
empowered and secure company. Diagrams do not count
as part of the required 1,200 words.
You may submit a business plan, a detailed outline, or an article-type essay that might be found in our text. The object of this final is for you to convey to me that you have grasped enough of the class material to practically apply it to a real situation. Be creative, for I am not assigning a particular writing style or report format.
Hand this in the last day of class.
QUIZZES FALL 2014
Electronic Crime
Fall – 2014 – LCCC and Tri-C
Quiz One
NAME (printed or typed)
_____________________________________________________________
The Five Things We Need To Know About Technology
Change
1. All technology change and
advancement is a tradeoff. This means: (5 Points)
2. The advantages
and disadvantages of a new technology are never distributed evenly among the
population. This means: (5 Points)
3. Embedded in every technology
there is a powerful idea, perhaps two or three powerful ideas. These ideas
are often hidden from our view because they are of a somewhat abstract
nature. But this should not be taken to mean they do not have practical
consequences. This means: (5 Points)
4. Technology change is not
additive; it is ecological. This means: (5 Points)
Managing the Risk of Fraud and Misconduct
5. Select the best answer: The sun will always rise
in the east and when it does we will call it morning. The sun will always
set in the west and when it does we will call it evening. This has always
been; it is part of nature - it is mythic. When a technology becomes mythic:
(3 Points)
Select one:
a. It is always dangerous because it is then
accepted as is
b. It is not easily susceptible to modification or
control
c. It is perceived to be part of the natural order of things
d. It tends to control more of our lives than is good for us
e. All of
the above
f. None of the above
6. "The printing press
annihilated the oral story-telling tradition; telegraphy annihilated space,
television has humiliated the printed word; the computer, it seems, is
degrading family and community togetherness." Which of the Five Things We
Need To Know About Technology is this an example? (3 Points)
Select one:
a. There is embedded in every great technology and epistemological,
political or social prejudice.
b. There is always a price for technology
c. There are always winners and losers
d. Technology change is not
additive; it is ecological; that is, it changes everything.
e.
Technology tends to become mythic, that is, perceived as part of the natural
order of things.
7. The three conditions that must be present for
fraud to occur are: Select one: (3 Points)
a. Opportunity, incentive, and
cooperation
b. Cohering, pressure, and opportunity
c. Opportunity,
incentive, and rationalization
d. Rationalization, opportunity, and
collaboration
e. None of the above
8. Select the best answer.
The previous question dealt with three conditions to occur necessary for
fraud. These three conditions are known as: (3 Points)
Select one:
a.
The Fraud Triangle
b. The Three Incentives for Crime
c. The Triple
Paradigm of Fraud
d. The Asset Misappropriation Trisector
9.
Select the best answer: The American Institute of Certified Public
Accountants has labeled "what" as the Achilles' heel of fraud prevention? (3
Points)
Select one:
a. Computer password hackers
b. Management
override
c. Lack of accounting control supervision
d. Computer
maintenance down time
e. The constantly changing accounting policies
requiring software updates and opportunity for hackers
10. Match the
best definition that most accurately applies to the term. Enter the letter
of the term in the blank preceding the definition. (3 Points each, total 27
Points)
I) ____The misappropriation of cash from an organization
prior to being recorded
II) ____The misappropriation of cash from an
organization after it has been recorded
III) ____Crediting one account
with the receipts intended for a different account
IV) ____Where funds
are distributed under the guise of a legitimate payment for invoiced goods
or services. Personal purchase schemes, non-accomplish vendor schemes,
schemes involving shell companies
V) ____Fraudulent disbursements that
are perpetrated through the creation of false documentation
VI)
____Placing orders for inventory that exceed the amount actually needed to
complete the project
VII) ____Fraudulent business ventures where
investors are paid from other investors' funds rather than operations
VIII) ____When an employee engages in the unauthorized use of company assets
IX) ____Inventory theft, Fictitious Sales, Purchasing and Receiving
Fraud
A. Asset Misuse
B. Noncash Fraud
C. Asset Requisition and
Transfer Fraud
D. Larceny
E. Lapping
F. Fraudulent Billing
G.
Payroll Schemes
H. Skimming
I. Ponzi Schemes
PowerPoint Slides on Electricity
11. a. Like charges _____________ each other.
b.
Opposite charges ____________each other. (4 points)
12. a. Every time
there is an alternating electric current, an _______________
_________________ is created. (2 Points)
b. Every time an alternating
magnetic field crosses a conductor, an _________________ ______________
__________________ is created. (2 Points)
c. This
______________________ ______________________ leaves the conductor and
travels through space at the speed of light. (2 Points)
13. True or
False An atom is composed of a nucleus containing positively charged
protons, negatively charged neutrons, and is orbited by neutrally charged
electrons. (2 Points)
14. True or False The carrier particle foe the
electromagnetic force is the electron. (2 Points)
15. True or False
The flow of electrons in a wire, amperes, and current are basically the same
thing. (2 Points)
16. What is a wavelength (in your own words)? (5
Points)
17. What is a frequency (in your own words)? (5 Points)
ESSAY:
18. In 500 words: How do you feel about the possibility of Facebook or other
social media being used to secretly influence your choices? Do you feel you
are being unknowingly manipulated if this technique was used to sell
products or influence your social or political decisions? Has this happened
to you? (12 points)
Electronic Crime
LCCC and Tri-C - Fall 2014
Quiz Two
Chapter 6
- Building an Integrated and Comprehensive Compliance Program for
Sustainable Value
Select the best answer.
1.
Effective fraud and misconduct risk management should begin with:
a. A well designed and properly executed ethics and compliance
b. A program that seeks to prevent, detect, and respond to fraud and
misconduct.
c. The program should be
thoroughly integrated into the organization's overall guidance and
risk-management framework
d. The program
should be thoroughly integrated into the company's business strategy and
operations
e. The program should not be an
isolated set of activities within the organization
f. All of the above.
Chapter 6 - Building an Integrated and
Comprehensive Compliance Program for Sustainable Value
2. Select
the best answer. Because managers, officers, and CEOs of
corporations are frequently the ones committing electronic crime, the
success or failure of a compliance program will rest on the organization's
ability to embed a culture of ethics and integrity.
Circle One: TRUE or FALSE
Chapter 6 - Building an Integrated and Comprehensive Compliance Program
for Sustainable Value
3. Select the best answer. An
affective GRC program is Government, Risk, and Compliance program that
protects, but does not enhance business values by fostering a risk-aware
culture.
Circle One: TRUE or FALSE
Chapter 6 - Building an Integrated and Comprehensive Compliance Program
for Sustainable Value
Select the best answer.
4. The
key attributes to an effective Compliance Function are:
a. Authority, Responsibility, Competency, Objectivity and Resources
b. Authority, Responsibility, Due Diligence, Objectivity, and Coordination
c. Authority, Coordination, Auditing, Responsibility, and Coordination
d. Coordination, Responsibility, Authority, Auditing, and Cooperation
Chapter 6 - Building an Integrated and Comprehensive Compliance Program
for Sustainable Value
Select the best answer.
5. An
effective Board of Directors overseeing a corporation's compliance program
needs information regarding:
a. Aligning
oversight, assessing risk, preventing misconduct, detecting and responding
to misconduct, allow the CEO to evaluate the effectiveness of the program.
b. Evaluate the effectiveness of the program by responding to the prevention
of misconduct and assigning managers to asses risking taking.
c. Aligning oversight, assessing risk, preventing misconduct, detecting and
responding to misconduct, and evaluating effectiveness of the program.
d. Aligning oversight, assessing risk, preventing misconduct, detecting and
responding to misconduct, and evaluating effectiveness of the program.
What is Alternating Current?
Matching:
6. Match the best definition in column B with the most
appropriate answer in column A.
A
B
| A. Zero | 1. ____Cycles per second |
| B. Remains constant | 2. ____Time interval between any two successive wave crests |
| C. Constantly changing | 3. ____The mazimum positive amplitude of a wave in the opposite direction |
| D. Crests | 4. ____Maximum positive amplitude of a wave |
| E. Trough | 5. ____The amplitude of an AC current |
| F. Period | 6. ____Amplitude of a DC voltage |
| G. Frequency | 7. ____Any point along the time axis |
Article: Relationships, Community, and Identity in the New Virtual
Society
Select the best answer.
7. In this
phenomenon, relationships for young people can be just as powerful and
meaningful as those in the real world.
a.
Virtual Society or virtual space
b. The the
Internet Only
c. Chat Rooms Exclusively
d. Emailting
e. Texting above asll other mediums
Article: Relationships, Community, and Identity in the New Virtual
Society
Select the best answer.
8. When
the VCR was invented, many people predicted the demise of movie theaters;
after all, if you can watch a movie at home why would anyone pay to go out
to a theater? Today, movie theaters are doing a record business.
When video conferencing was developed, some people predicted that many
airlines and hotels would go out of business; after all, why would
businessmen spend thousands of dollars on airfare, hotels, and meals to
attend a business conference when they could stay in the office and do it on
line? Well, airlines and hotels are busier than ever.
The social turmoil of the 1970s was proclaimed by many to be the end of the
nuclear family. But the family is still here; it's just different.
People are now predicting that texting, email, chat rooms, cell phones,
blogs, Facebook relationships, tweeting, on-line dating, and other social
media are going to diminish our person-to-person interactions and destroy
human personal interaction.
What actually will
happen is some human relationships will become shallower through cyber space
relationship while others will become stronger. Things will change, but
still be meaningful. As stated in Article 1 - Technology giveth and
technology taketh away.
Circle One: TRUE or FALSE
Article: Relationships, Community, and Identity in
the New Virtual Society
Select the best answer.
9.
Your
found identity is one created by your circumstances - who your
parents were, your ethnicity, your religion, your gender, your history and
education and past experiences. Your made identity is...
a. ...the style of clothes and jewelry you wear
b. ...your chosen behaviors
c. ...your selected
automobile, activities, and clubs you have joined
d. ...how you want others to see you
e. All of
the above
Article: Are U Friends 4 Real?
Select the best
answer.
10. "Flaming" is a cyber term meaning text or
email that invokes anger or other high emotions resulting from the hostile
interpretation of such messages. But texting, email, and Facebook are
void of the human voice, the voice tone indicating anger, sadness, or
frustration; the pauses between words indicating thought or concern, and the
speed of the speech possibly indicating anxiousness.
The phrase "You can make a marketing plan," can be said many different ways
where one is a complement, the other is an insult, yet a third filled with
sarcasm. It depends on where the pauses are, where the voice volume
increases, and the voice tone. Such communication is also void of body
language and facial expressions which often make up over 80% of our personal
communications.
I once wrote what I
considered to be a very grateful email of thanks and appreciation to a
colleague for the effort he and his staff put into a wonderful weekend
wedding. Shortly after sending the letter, I received a very defensive
phone call asking how I could be so unfair and insulting when he tried so
hard to make the event successful. Somewhat dismayed, I went to his office
and read to him my email with a kind voice tone, concerned inflections,
appreciative pauses, and accompanied by facial expressions showing happiness
and gratitude. What a difference! He was amazed!
Friendships, romantic relationships, business memos, colleague
correspondence, and instructions to employees, spouses, and children are
often in the form of texts. Should care be taken in these messages to avoid
"flaming" interpretations?
a. Yes, care should always be taken to avoid "flaming
interpretations" even though success is not guaranteed.
b. No; flaming can't be avoided.
c. No, if 50
people read the same message there will be 50 different interpretations. How
can one attempt to overcome that?
d. No, email
and texting and other written forms of communication should always be
replaced with phone calls to avoid flaming.
Article: Hacking the Lights Out
Select the best
answer
11. The Stuxnet virus was planted into
Iran's nuclear program computers by:
a. Internet
virus attack through email
b. A back door attack
through a computer's firewall
c. Through a USB
stick handed to an unsuspecting employee
d.
Through the power grid at the local power station
e. From a trojan horse implanted into a didigital procedures manual
Article: Hacking the Lights Out
Select the best
answer
12. When Iran's nuclear centrifuges were spinning out of
control at a dangerous RPM, why didn't the control personnel intervene
before the centrifuges were destroyed?
a. The
virus hit the centrifuges in the middle of the night when the neclear plants
were closed
b. The virus send false signals to
the supervising controllers indicating all operations were operating
normally
c. The Stuxnet virus stopped the
control mechanisms sent to supervisory personnel.
d. The Stuxnet virus struck Iran's nuclear facilities on a holy holiday and
the plants were closed
Article: Hacking the Lights Out
Select the best
answer
13. All electricity furnished for home and industrial use
in the United States uses 60-cycle alternating current. The power grid is
the electrical supply circuits of thousands of power companies in United
States all connected together. The 60 cycle AC current coming from any power
company must match (be in sync) with the 60 cycle timing on the grid. The
Aurora cyberattack in 2007 was staged by a pretend hacker working for the
Department of Homeland Security to bring down an electric generator in a
power company attached to the grid. How did this attack function?
a. The hacker created and out-of-sync 60 cycle current in opposition
to the generators 60 cycle output.
b. The
hacker planted a bomb under the generator
c.
The hacker planted a bomb under the generator
d.
The hacker pulled the generator's circuit breaker shutting the generator
down
Article: Hacking the Lights Out
Select the best
answer
14. Computers are subject to attack.
The nation's electric power grid is also subject to attack by cybercriminals
and it is much easier to hack than many protected computers.
Circle One: TRUE or FALSE
Article The Bride of Stuxnet
Select the five answers
that apply.
15. Once the virus Flame infects a
computer, what happens?
a. It records every
keystroke
b. It creates a perfect log of all
activities
c. It takes pictures of the monitor
screen every 60 seconds
d. It sends out bogus
emails to everyone on the computer's email list
e. It takes control of Bluetooth capability turning into a hub for a
wireless network
f. It copies documents
and files on the computer's hard drive
Article The Bride of Stuxnet
Select the besat answer
16. Stuxnet was a virus designed to work quickly, and in doing so it can be
discovered quickly, so it must do its damage fast. Flame was a virus
concerned with stealth and patience, moving very slowing, and infecting
fewer machines.
Circle OneL: TRUE or FALSE
Chapter 7 - Prevention: Risk Assessment
Select the best answer
17. The definition of
what is as follows: A step-by-step process for identifying the
quantitative and qualitative nature of potential integrity breakdown?
a. Design considerations
b. Risk Assessment
c. Business goals and stategy
d. Control
Optimazion
e. Risk Taking
Chapter 7 - Prevention: Risk Assessment
Select the best answer
18. What is the below procedure entitled?
(1) Identify Business Units,
locations, or processes to assets
(2) Inventory and categorize fraud and
misconduct risks
(3) Rate risks based on likelihood and significance of
occurrence
(4) Remediate risks through control optimization
a. The four fundamental steps of risk assessment
b. The four fundamental steps of risk assessment
c. The four levels of crime, fraud, and misconduct
d. The four basics of the fraud rectangle
e. The control optimization for risk procedures
Chapter 7 - Prevention: Risk Assessment
Select the best answer
19. The first step is starting a risk assessment program is:
a. Putting someone responsible in charge
b. Deciding those aspects or parts of the organization that will be
subject to the risk assessment.
c.
Establishing a focus group to evaluate the overall risk of the company
d. Review documentation from previous risk assessment groups
e. Have the focus group consult with the risk assessment team.
Chapter 7 - Prevention: Risk Assessment
Select the best
answers - There are FOUR (4) correct answers
20. It is wise for
the risk assessment team to have a company document review take place in
order to determine company policies, procedures, and internal control.
These documents to be reviewed include:
a.
Code of Conduct
b. Applicable job
descriptions
c. Employee attendance
records
d. Organizational charts
e. Responce and improvement systems
f.
Competitor's violation records
g. All of the
above
Chapter 7: Prevention: Risk Assessment
Select the best answer
21. Once the assessment team has estimated risk likelihood and significance,
it is helpful to plot risks on an axis representing their significance and
likelihood of occurrence using a heat map.
Circle One: TRUE or FALSE
Chapter 7
Secelct the best answer
22. The primary
coil of a transformer has 200 volts applied to it and 100 coils. The
secondary side of the transformer has 50 coils. What is the voltage output
on the secondary side?
a. 50 volts
b. 100 volts
c. 200 Volts
d. 100 amps
e. 4 volts
Select the best answer
23. If you cut the resistance in half in an
electrical circuit with 100 volts, the the amperes will double.
Circle One: TRUE or FALSE
Chapter 7
Select the best answer
24. If the primary input side of a
transformer has 500 turns and 100 volts, how many turns (coils) would you
need on the secondary output side for the output to be 20 volts?
a. 100 coil turns
b. 50 coil turns
c. 200 coil turns
d. 20 coil turns
e. None of the above
All your Ohm's law formulas are listed in the above
wheel.
Refer to Chapter 3 on Electricity DeMystified if necessary.
A spy for a competitive industry wants to listen to private conversations
being broadcast over a competitor's private walkie-talkie network where
management discuss test results in the field with engineers. The spy's
office is too far away to receive the competitor's walkie-talkie signals.
Somehow the spy needs to double the power output of the competitor's
walkie-talkie signal. In order to accomplish this, the spy visits the
competitor impersonating a communications walkie-talkie and radio company, J
& B Communications, offering a free introductory deal. The introductory
offer is to clean and tune all the competitor's walkie-talkies for free with
the understanding that J & B Communications would be considered for any
repair jobs in the future. The competitor agrees to the deal and give the
spy 10 walkiw talkies to be cleaned, reconditioned, and returned in the
morning. This is called social engineering.
The spy takes the walkie-talkies to his office and opens them up. The
circuit on the antenna looks like the one below.
Do not be discouraged
about this electronic circuit. Let's say it is the power output circuit to
each walkie-talkie's antenna. The power to the antenna is 2 watts.
I =
E/R = (Amps equals voltage divided by resistance)
I = 10/50 =
(Amps equals 10 volts divided by 50 ohms) = .2 amps
The
power output of the antenna is measured in watts. P = watts
P = EI (Power
equals voltage times amps)
P = 10 X .2 = 2 watts. The walkie-talkies currently
transmits a 2 watt signal. The spy wants to double this power output
to 4 watts. This would make the walkie-talkies more powerful, transmitt a
longer distance, and allow the spy to monitor his competitor's
conversations.
The spy decided to change the 50 Ohm resistor R3 in each
walkie- talkie to a different value. What value in ohms should the new
resistor be in order to double the output power of each walkie talkie?
I = E/R = (Amps equals voltage divided by resistance)
I =
10/?
= (Amps equals 10 volta divided by
?
ohms) = .4 amps
The power output of the antenna is
measured in watts. P = watts
P = EI (Power equals voltage times amps)
P = 10 X .4 = 4 watts.
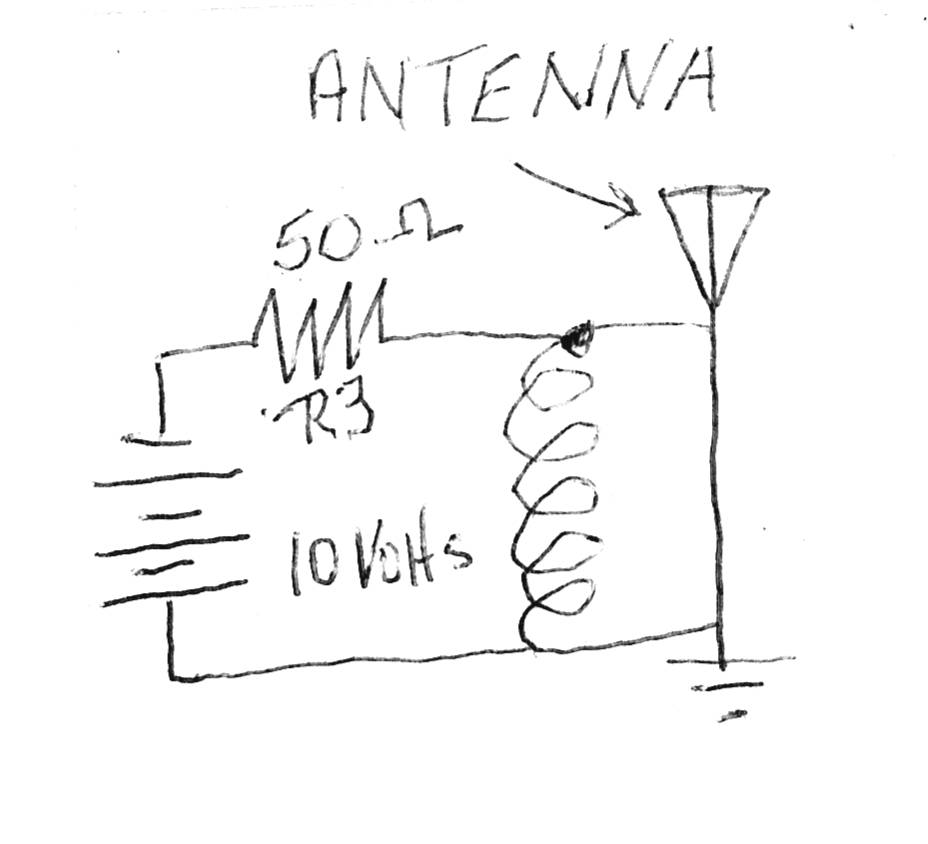
Do you see now why you learned
ohm's law? It is frequently used in electronic crime. (The actual circuit
above would require different formulas beyond the scope of this course.)
a. 50 ohms
b. 200 ohms
c. 35 ohms
d. 25 ohms
e. None of the above
Select the best answers from the matching table
26. Insert the best
answer from column A into Column B
|
A. Captain Krunch |
___Steve Wozniak |
| B. A Hacker who helped form Apple Compluter | ___ John DFraper |
| C. A young teenager who became a phreaker and hacker | ___Kevin Mitnik |
| D. One of the founders of Apple Computer and the CEO and chairman | ___Steve Jobs |
Spplemental Course Study Material
Hacker Web Sites & Culture
Class PowerPoint
Presentations
Telecommunication's
Crime Presentation
Atom
& Electronics Presentation
Atoms, Energy, and Electricity
The Particle Adventure
http://particleadventure.org/particleadventure/index.html
Disclaimer
These Web Sites are to be used for educational purposes only. In order to combat illegal hacking, it is necessary to understand how and why these activities take place.
![]() Watch for bugs!
Watch for bugs!
Below are some hacker and pfreaker websites. Study them to learn about their environment, culture, beliefs, and purpose. Learn the difference between the hacker that's a vandal and the hacker that's looking for security leaks in software encouraging the manufacture of such software to repair the vulnerable points in its product.
The Story of Kevin Mitnik
Kevin Mitnik Site
http://www.takedown.com/bio/mitnick.html
The Story of the Captain Crunch Cereal Whistle
Captain Crunch
Hacker Manuals and Instruction Guides
http://www.spectre-press.com/
The Hackers' Home Page
http://www.hackershomepage.com/
Some Hacking Organizations
http://www.yahoo.com/Computers_and_Internet/Security_and_Encryption/Hacking/Organizations/
Famous Hacked Web Sites
http://dir.yahoo.com/Computers_and_Internet/Security_and_Encryption/Hacking/Hacked_Web_Sites/
Glossary of Computer and Internet Terms
http://foldoc.org/
The Hacker Dictionary
http://www.hacker-dictionary.com/
The Jargon File
http://www.catb.org/~esr/jargon/
Some Famous Hacking Organizations
2600
http://www.2600.com
2600 Hacked Websites
http://www.2600.com/hacked_pages/
L0pht Heavy Industries
http://search.msn.com/results.asp?q=L0pht&spoff=on&origq=&RS=CHECKED&FORM=SMCRT&v=1&cfg=SMCINITIAL&nosp=0&thr=0&x=28&y=16
Cult of the Dead Cow
http://www.cultdeadcow.com